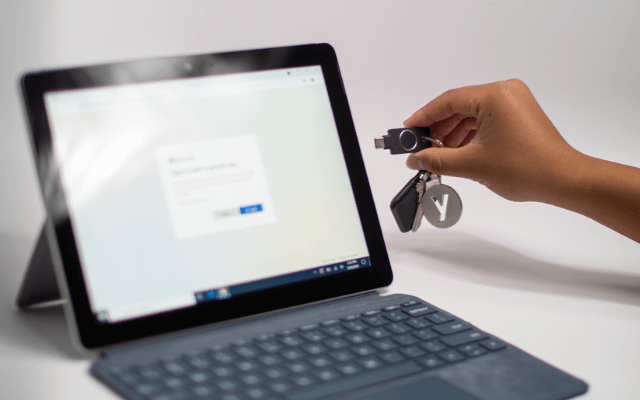
video
Proven security on a large scale

Stop account takeovers
The world's largest companies trust YubiKeys, and there have been 0 account takeovers to date.

Easy setup and support
It's as easy as USB! Access your accounts 4x faster than other 2FA solutions and reduce support calls by 92%.

Specially developed for safety
Unlike other 2FA solutions, YubiKeys does not store data, does not establish a network connection, and does not run on software.
One key for many applications
The YubiKey works with hundreds of enterprise, developer, and consumer applications out-of-the-box and without client software. Combined with leading password managers, social login, and enterprise single sign-on systems, the YubiKey enables secure access to millions of online services.
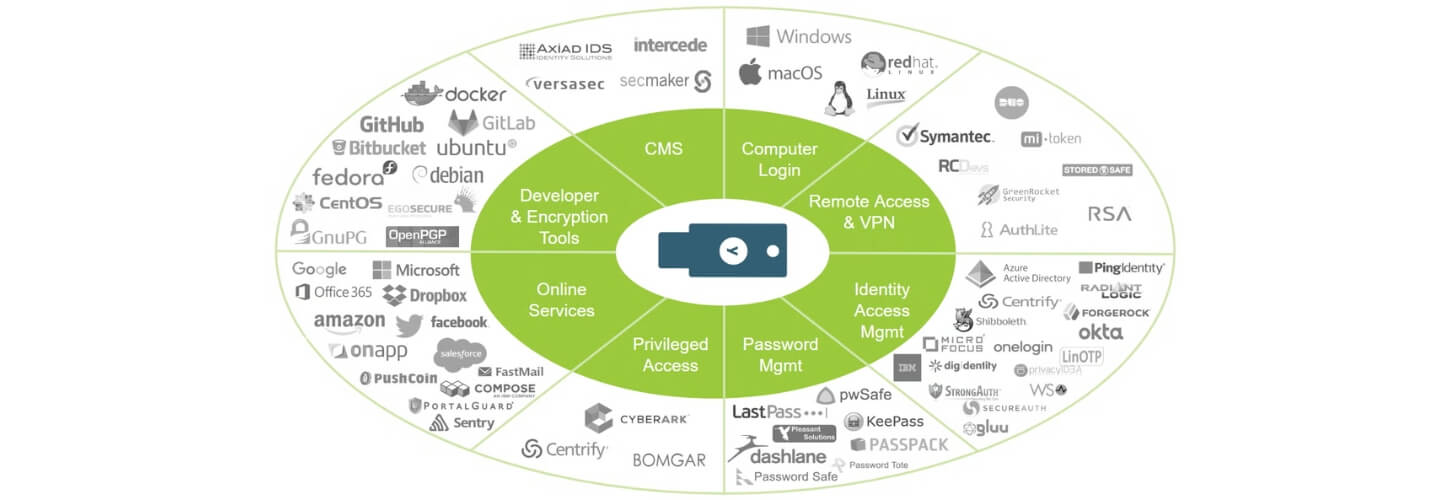
How it works
A single YubiKey has multiple functions to secure your login to email, online services, apps, computers, and even physical spaces. You can use any or all of the YubiKey's features. The versatile YubiKey requires no software installation or battery, so simply plug it into a USB port and touch the button or tap it with NFC for secure authentication.
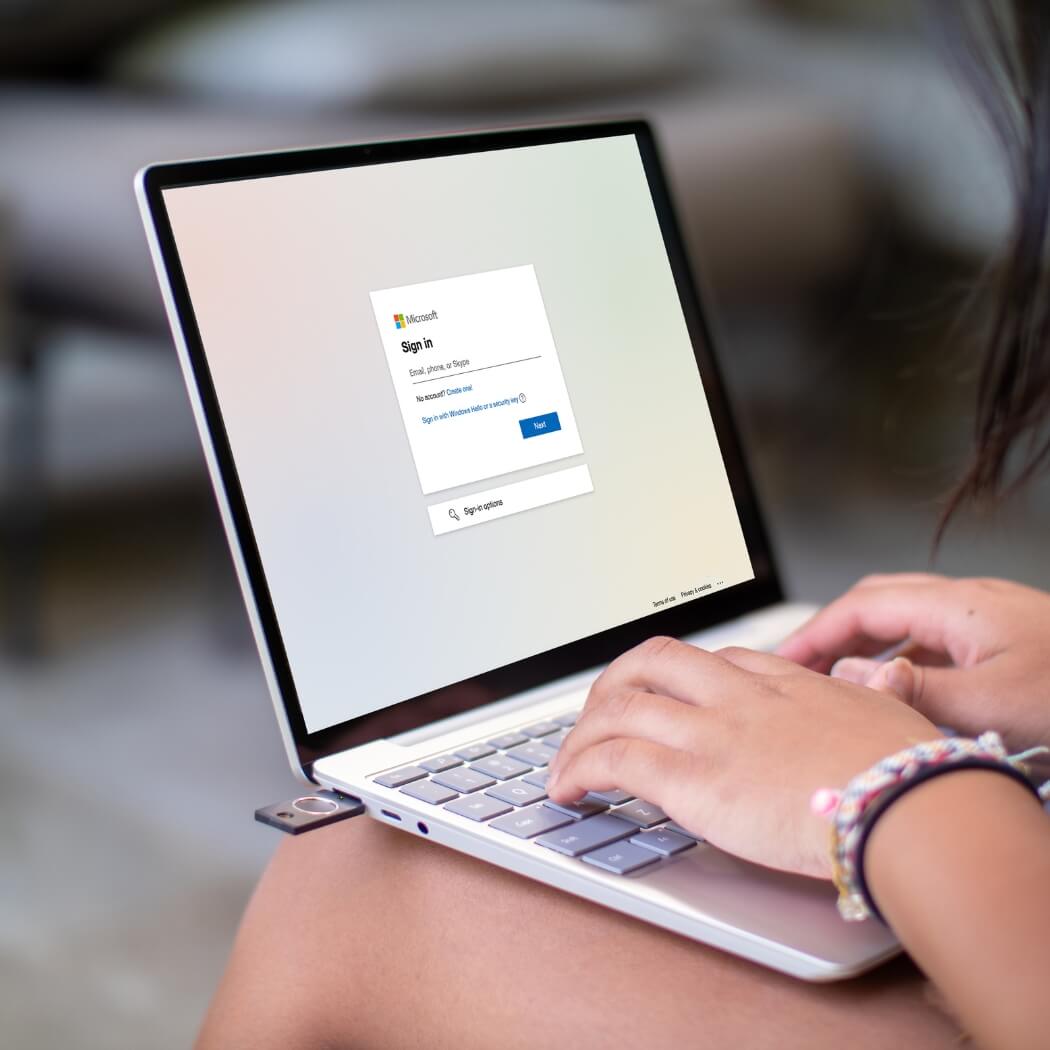
Register your YubiKey
To use the YubiKey, go to the security settings of a supported service and select two-factor authentication.

Insert YubiKey & tap
Plug the YubiKey into a USB port on a computer and touch the YubiKey to verify that you are a human and not a hacker.

Tap the phone
For NFC-enabled phones, simply tap your NFC-enabled YubiKey to the phone to complete authentication.

Multi-protocol security key secures modern and legacy systems
The YubiKey supports WebAuthn/FIDO2, FIDO U2F, One-Time Password (OTP), OpenPGP 3, and smart card authentication, providing a solution that bridges legacy and modern applications. Yubico and the YubiKey will continue to grow with your evolving business needs.

The YubiKey supports one-time passcodes (OTP)
OTP supports protocols that require a one-time-use code to be entered for authentication. These protocols are generally older and more commonly supported by older applications. The YubiKey communicates over the HID keyboard interface, sending output as a series of keystrokes. This means OTP protocols work with all operating systems and environments that support USB keyboards, as well as with any application that can accept keyboard input.

The YubiKey enables authentication with a smart card
Smart cards are another protocol supported by the YubiKey. The YubiKey identifies itself as a smart card reader when a smart card is inserted, allowing it to work with most common smart card drivers. The YubiKey allows the simultaneous use of three different protocols: PIV, as defined by the NIST standard for authentication; OpenPGP for encryption, decryption, and signing; and OATH for client applications such as Yubico Authenticator.

Enable modern authentication with FIDO U2F
FIDO U2F is another protocol supported by the YubiKey. The U2F protocol provides strong authentication without requiring a complex backend or framework to support it. FIDO U2F turns traditional authentication on its head, turning the authentication device, such as the YubiKey, into the authentication provider. It issues unique keys to the services it authenticates against, ensuring that each service has no information about the others, and eliminating the need for a central authentication service.

Experience passwordless authentication with FIDO2
FIDO2 is the passwordless evolution of FIDO U2F. The overall goal of FIDO2 is to provide an expanded feature set to address additional use cases, with passwordless logins as the primary driver. The U2F model remains the foundation for FIDO2, and compatibility with existing U2F implementations is provided for in the FIDO2 specifications.