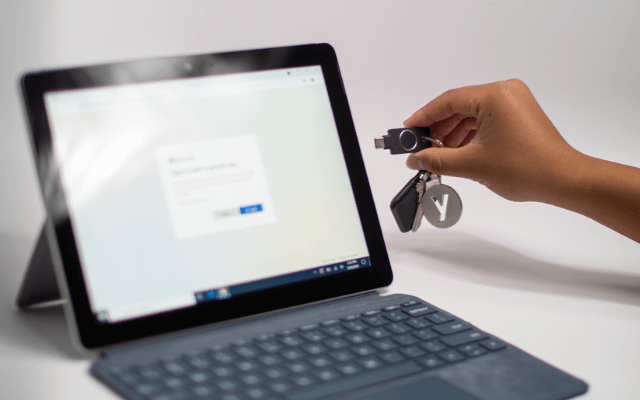
Accelerate Zero Trust with phishing-resistant authentication and hardware-assisted security for manufacturers
Manufacturers of all kinds are being targeted by ransomware and phishing at alarming rates. While multi-factor authentication (MFA) can be a strong first line of defense, not all forms of MFA are equally effective at protecting against account takeovers.
To protect against cybersecurity threats in production, you need an authentication solution that can bypass legacy infrastructure and restrictive manufacturing requirements, protect information technology (IT), operational technology (OT), and industrial control systems (ICS), while enabling the transition to more phishing-resistant methods: Smart Card/PIV or FIDO.
It's becoming increasingly urgent to implement phishing-resistant MFA and cryptographic protection to ensure no user or device is allowed onto your network without verification. Even the Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) recommend phishing-resistant authentication for all critical infrastructure, including manufacturing.
Yubico's solutions and services meet you where you are on your cybersecurity journey and pave the way to a modern, phishing-resistant authentication infrastructure. Secure your digital transformation and stop account takeovers with Yubico.
Protecting people, data, and critical infrastructure from cybersecurity threats in manufacturing
Phishing-resistant authentication and cryptographic protection provide robust security at scale and accelerate Zero Trust

The YubiKey for phishing-resistant multi-factor and passwordless authentication secures data and user access to critical IT, OT and ICS systems.
- Simple use of a hardware-based passkey that requires no battery or cellular connection
- IP68-certified and FIPS 140-2 validated for all environments, from industrial to highly regulated environments
- Provides multi-protocol support to protect existing systems while modernizing your infrastructure

The ultra-portable YubiHSM 2 provides cryptographic protection for servers, applications, and computing devices.
- FIPS 140-2 validated to support highly regulated environments
- Ultra-portable with innovative "Nano" form factor that allows flexible use
- Cost-effective, as it provides enterprise-grade cryptographic security without the cost of a traditional HSM

Benefits of Yubico solutions for protecting against cybersecurity threats in manufacturing

Reduce IT support costs and achieve high ROI
The combination of a seamless user experience, data breach prevention, savings on mobile device and service costs, and the versatility of the YubiKey with multi-protocol support results in a high ROI.
With the flexible procurement and deployment options of the YubiEnterprise subscription, you can achieve an estimated 203% ROI within three years and a 75% reduction in password-related help desk support tickets by year three.
YubiKeys:
- enable self-service password resets, eliminating IT support costs for helpdesk password reset requests.
- are future-proof security investments as they bridge the gap to modern authentication protocols and enable secure passwordless login.
- support the following protocols: FIDO U2F, WebAuthn/FIDO2 (passkeys), OTP/TOTP, OpenPGP and Smart Card/PIV.
Securing production lines and supply chains worldwide
As supply chain integrity becomes increasingly important, manufacturing companies are turning to Yubico to protect their supply chain and intellectual property—from sensors and medical devices to automobiles and other products with electronic components.
YubiKeys provide secure, convenient, and scalable security, making it easy for you and your supply chain suppliers to deploy strong authentication.
The YubiHSM 2 is designed to protect trade secrets and secure production lines.

Secure shared workspaces, restricted mobility areas, and cloud services
Extremely portable and easy to use, YubiKeys increase employee productivity. They offer fast, passwordless one-tap login that's 4x faster than SMS login. A single YubiKey conveniently works across multiple devices, including desktops, laptops, mobile phones, tablets, notebooks, and shared workspaces/kiosks.
YubiKeys integrate seamlessly with existing IAM solutions like Microsoft, Okta, Duo, and Ping, providing secure authentication for hundreds of applications and services. With more than 1,000 integrations , your users can instantly use YubiKeys with all the apps and services they love.

Ensuring compliance with global regulations
As a result of increasing cyberattacks, regulatory changes such as National Institute of Standards and Technology (NIST) SP 800-63-3, IEC 62443 Security for Industrial Automation and Control Systems, the EU Network and Information Security Directive (NIS2) , and others are continually introducing new security requirements regarding stronger multi-factor authentication that can no longer be met by passwords and legacy authentication systems.
In regulated environments, YubiKey and YubiHSM can help manufacturers comply with mandatory and voluntary data security standards.